End-to-End Encrypted Cloud Storage in the Wild
A Broken Ecosystem
Jonas Hofmann, Kien Tuong Truong.
Work to appear at ACM CCS 2024
Cloud storage is ubiquitous: Google Drive, Dropbox, and OneDrive are household names. However, these services do not provide end-to-end encryption (E2EE), meaning that the provider has access to the data stored on their servers. The promise of end-to-end encrypted cloud storage is that users can have the best of both worlds, keeping control of their data using cryptographic techniques, while still benefiting from low-cost storage solutions.
However, previous analyses of MEGA and NextCloud have shown that even the largest providers of E2EE cloud storage are affected by cryptographic vulnerabilities and creating secure E2EE cloud storage is a harder problem than initially thought.
Indeed, we show that the current ecosystem of E2EE cloud storage is largely broken. We conduct a cryptographic analysis of five major providers in the field, namely Sync, pCloud, Icedrive, Seafile, and Tresorit, in the setting of a malicious server. We unveil severe cryptographic vulnerabilities in the first four.
The vulnerabilities range in severity: in many cases a malicious server can inject files, tamper with file data, and even gain direct access to plaintext. Remarkably, many of our attacks affect multiple providers in the same way, revealing common failure patterns in independent cryptographic designs.
Overview
Sync is a Canadian cloud storage provider founded in 2011 with more than 2 million users worldwide, including high profile institutions such as the government of Canada, the university of Toronto, and the Canadian red cross. It claims to store more than 130 petabytes of data.
Our attacks allow a malicious server to break the confidentiality of uploaded files, as well as injecting files and tampering with their content.
Cryptographic Primitives
- Key Derivation
- PBKDF2-SHA256 (random salt)
- Symmetric Encryption
- AES-GCM
- Asymmetric Encryption
- RSA-PKCS1v1.5
Key Hierarchy
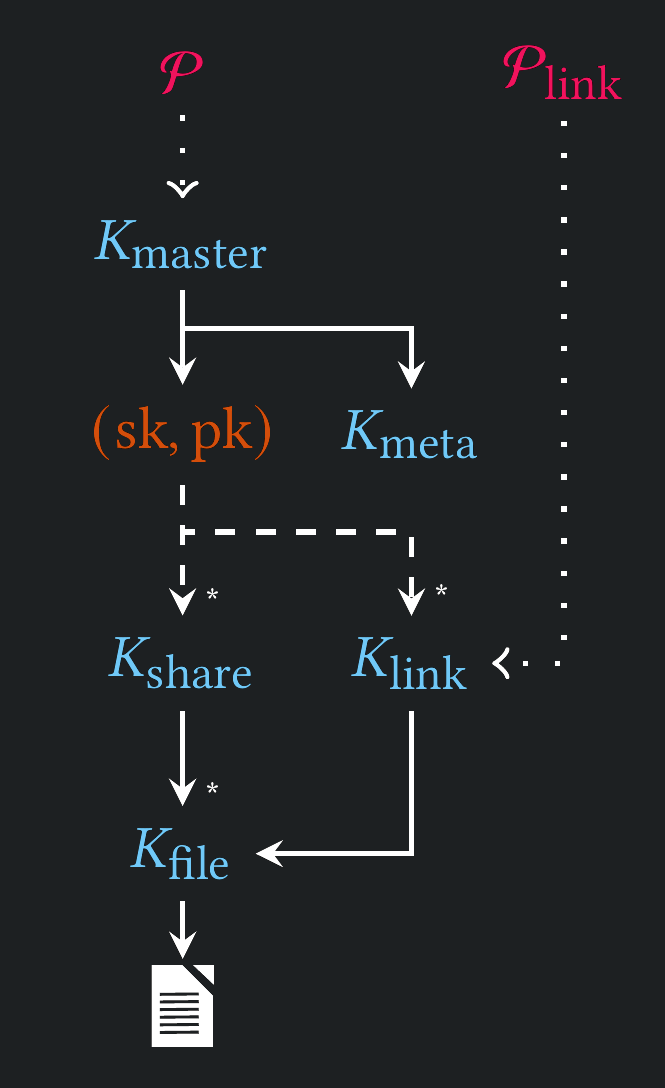
Attacks
Key Replacement | Link Sharing Leakage |
Tampering with Filenames | Tampering with Metadata |
Folder Injection | File Injection |
pCloud is a Swiss-based cloud storage provider founded in 2013 with more than 20 million users worldwide and claiming to be "Europe's most secure cloud storage"
Our attacks allow a malicious server to break the confidentiality of uploaded files, as well as injecting files and tampering with their content.
Cryptographic Primitives
- Key Derivation
- PBKDF2-SHA512 (random salt)
- Symmetric Encryption
- AES-CTR (variation)
- Custom authenticated mode of operation
- Asymmetric Encryption
- RSA-OAEP
Key Hierarchy
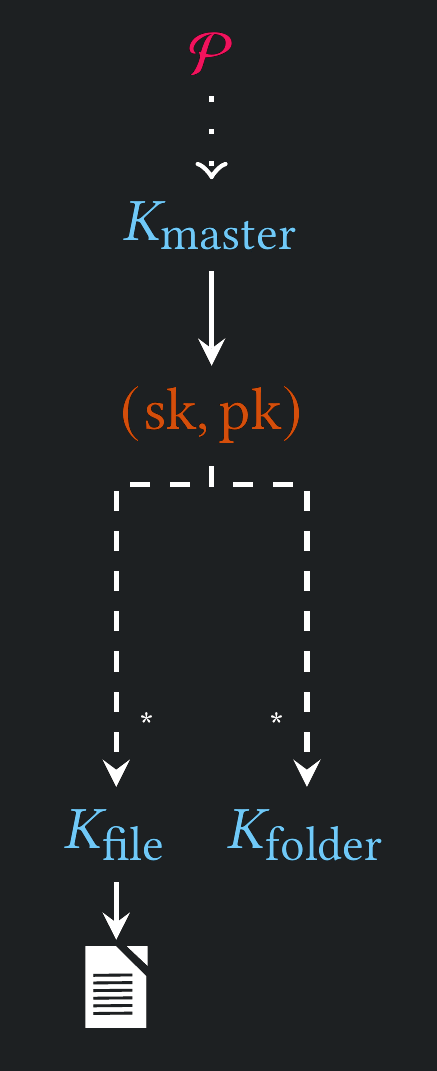
Attacks
Key Replacement | Key Overwriting |
Unauthenticated Chunking | Tampering with Files and Filedata |
Tampering with Metadata | Folder/File Injection |
Seafile is an open-source cloud storage provider founded in 2012 with more than one million users worldwide. In contrast to the other providers we analyze, Seafile also offers a self-hosting solution. Among the organizations using it are Kaspersky Lab, the Humboldt University in Berlin, the University of Strasbourg, and the University of Turku.
Our attacks allow a malicious server to speed-up bruteforcing of user passwords, as well as injecting files and tampering with their content.
Cryptographic Primitives
- Key Derivation
- PBKDF2-SHA256
- BytesToKey-SHA1
- Symmetric Encryption
- AES-128-CBC
- AES-256-CBC
- AES-128-ECB
Key Hierarchy
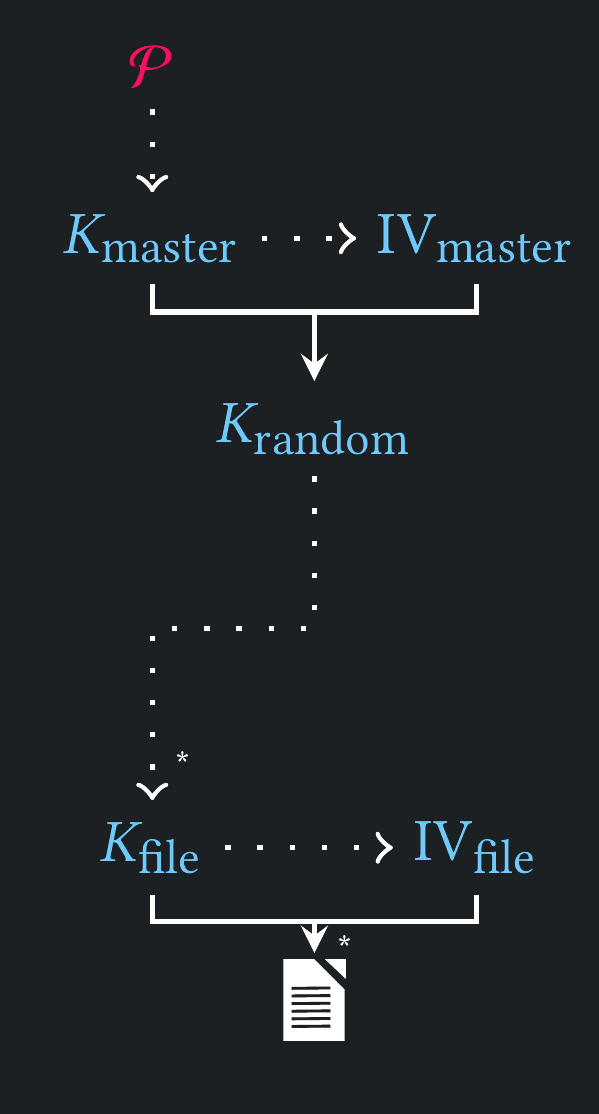
Attacks
Protocol Downgrade | Unauthenticated Encryption |
Unauthenticated Chunking | Tampering with Files |
Tampering with Metadata | Folder/File Injection |
Icedrive is a UK-based cloud storage provider founded in 2019 with an estimated 150k users worldwide.
Our attacks allow a malicious server to break the integrity of uploaded files, as well as injecting files and tampering with their content.
Cryptographic Primitives
- Key Derivation
- PBKDF2-SHA256
- Symmetric Encryption
- TwoFish-CBC
- TwoFish (in custom mode)
Key Hierarchy

Attacks
Unauthenticated Encryption | Unauthenticated Chunking |
Tampering with File Locations and Names | Tampering with Metadata |
File Injection |
Tresorit is a Swiss-based cloud storage provider founded in 2011 with an estimated 10 million users worldwide.
Our attacks allow a malicious server to present non-authentic keys when sharing files and to tamper with some metadata in the storage.
Cryptographic Primitives
- Key Derivation
- scrypt
- PBKDF2
- Symmetric Encryption
- AES-GCM (key material)
- AES-CFB (data)
- Asymmetric Encryption
- RSA-OAEP
Key Hierarchy
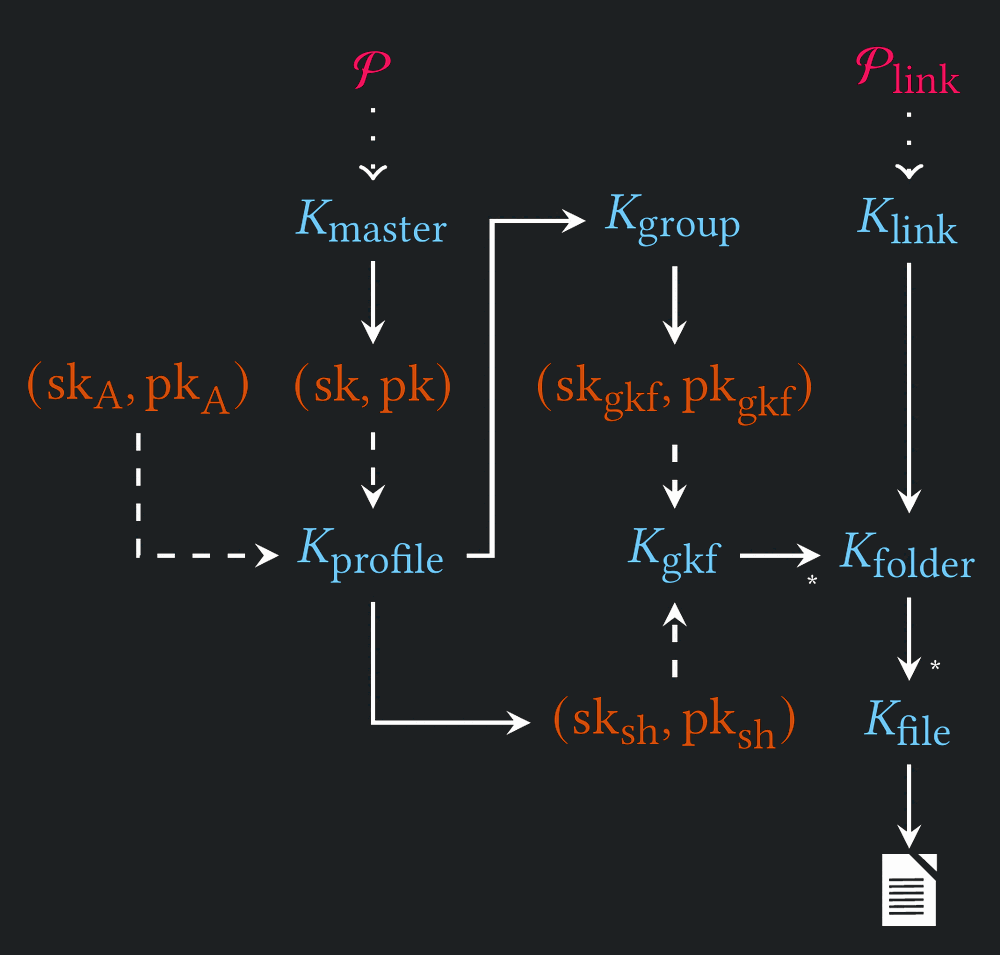
Attacks
Key Replacement | Tampering with Metadata |
Discussion
What is your threat model?
All of our vulnerabilities are in the setting of a malicious server. This means that the server is controlled by an adversary, who can read, modify, and inject data at will. This may seem like a strong adversary model, but it is the most realistic for E2EE cloud storage.
This model is also consistent with the security claims made by the providers we analyzed. Here are some examples:
Sync's unique end-to-end encrypted storage platform ensures that only you have access to your files, which is the only way you can truly trust the cloud.
SyncNo one, even pCloud's administrators, will have access to your content.
pCloud[...] you, and only you, are the only individual that can view and decrypt your data - Not even us - And that's just the way it should be.
IcedriveWe do not claim that the providers themselves would act maliciously, but rather that, by virtue of the data they store, they are an attractive target for nation-state adversaries and hackers, who would attempt to compromise the server and mount attacks against the users.
What are the takeaways of your analysis?
First, there is a gap between what is marketed by some providers and the reasonable expectations users have of their products. Confidentiality is a baseline requirement which we break for some providers. We violate integrity for files and metadata in many other providers, injecting (possibly incriminating) files in the storage of users. Metadata is leaked in many cases, which can be a privacy concern. Our findings allow users to make more informed decisions about the security of their data if they ever decide to use one of the providers we analyzed.
Second, we show that various products fail in similar ways, indicating that the challenges in this setting are non-trivial. Compare this to more mature fields such as secure channels, where protocols like TLS, SSH, and the Noise framework have been developed and analyzed for decades, or to secure messaging, where the most of the main products are based on the Signal protocol. In contrast, in the field of E2EE cloud storage there are many products that fail at a trivial level, cryptographically speaking. This is a strong indication that more foundational work is required in order to provide more secure products.
What must be done to improve this field?
The effort should be two-fold. On the one hand, more analyses of E2EE cloud storage systems "in the wild" need to be conducted. This is crucial to understand the current state of deployed protocols and what the challenges are. On the other hand, more theoretical work is required to provide a solid foundation for the design of secure E2EE cloud storage systems. The final objective is to create a standard for E2EE cloud storage, similar to the Signal protocol for secure messaging.
This is an active research field: other than the previously mentioned analyses of MEGA and Nextcloud, Backendal et al. have recently developed a formal model for E2EE cloud storage, starting the foundations for a more secure ecosystem.
How did you choose which products to analyze? Why have you not analyzed X?
We have chosen the products based on their popularity, especially when using queries such as "most secure end-to-end encrypted cloud storage" on search engines. While clearly there are many more providers, some of which might be secure, we have decided to leave those as future work. We did not omit any provider on purpose, and we are open to analyzing more providers in the future. Also, simply enough, there are only so many providers we could fit within a conference paper. We encourage researchers to analyze different providers and to publish their findings.
Coordinated Disclosure
We have notified Sync, pCloud, Seafile, and Icedrive of our findings on the 23th April 2024, proposing a coordinated disclosure of the vulnerabilities and suggesting the standard 90 day disclosure window. The Icedrive team acknowledged our email on the same day and, after a brief exchange, opted not to address the issues we raised. The Seafile team acknowledged the email on the 24th April 2024 and replied on the 29th of April, informing us that they will patch the protocol downgrade issue. As of 10th October 2024, Sync and pCloud have yet to respond to multiple attempts to contact them through different channels. We contacted Tresorit on 27.09.24 to discuss their cryptographic design. They acknowledged our email on 30.09.24.
About Us
This work was conducted by Jonas Hofmann and Kien Tuong Truong with the Applied Cryptography Group at ETH Zurich.
We are not affiliated with any of the providers we analyzed in this work.
The accompanying paper will be published at CCS 2024.